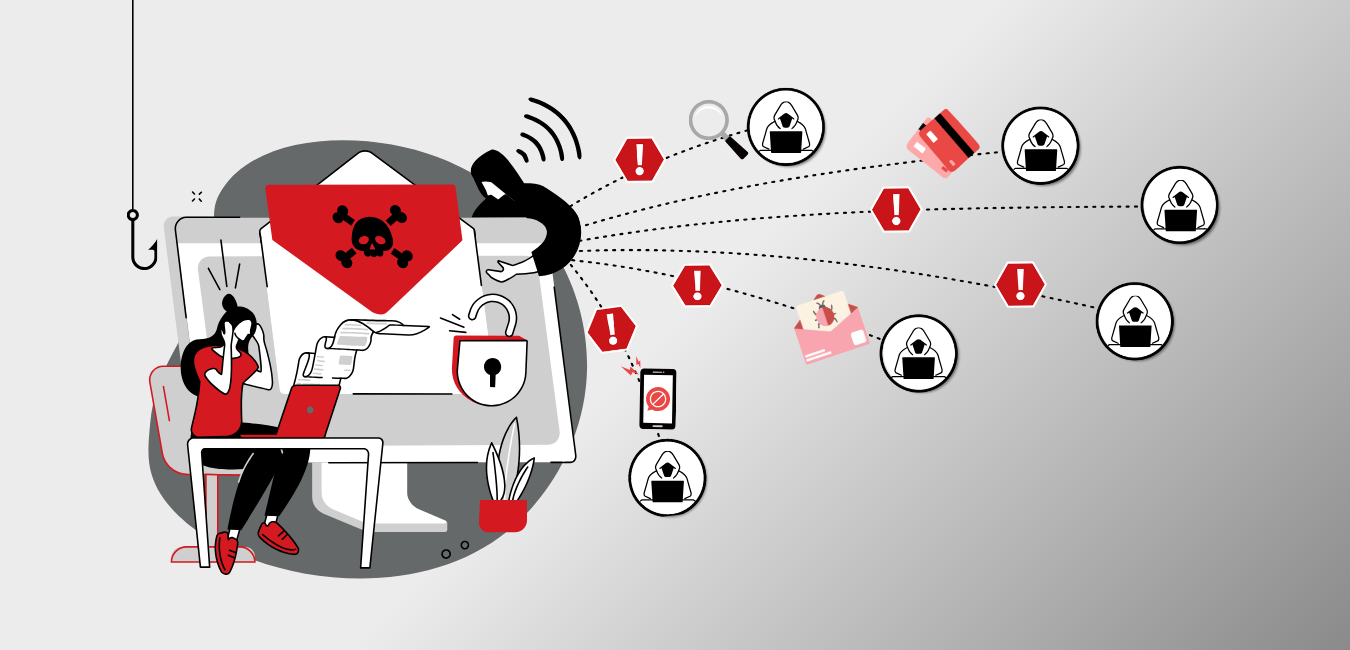
There’s no denying it – in 2025, cybercriminals have not just failed to disappear, they have actually become significantly more creative. At the same time, security mistakes are increasing and threats are evolving and becoming larger and more dangerous – and at a dangerously high pace. The more time we spend in the online environment, the more we share and move our businesses online, the more these dangers multiply. But let’s be honest – a modern business simply can’t survive without an online presence. For small and medium-sized businesses, and even large ones, a tiny lapse in cybersecurity can mean too much – the leak of sensitive information, complete business collapse for days, loss of large sums of money, loss of customer trust, a destroyed reputation, and even the worst – a fiasco and the end of a business you have poured everything into.
Although this forecast sounds quite apocalyptic, the ugly truth is that it is entirely realistic for many businesses. But it is not inevitable, and there are solutions! The majority of cyberattacks are not the result of a mysterious, genius hacker who has targeted your business and dedicated himself to destroying it from his basement. That is more of a scene from a movie. In most cases, cyberattacks are the result of small security mistakes we often make. But these are completely preventable mistakes.
So, grab a hot cup of coffee, squeeze your stress ball if you are already feeling tense, and let’s take a look at the eight most common cybersecurity mistakes we make. Let’s also see how we can easily prevent them!
Exploring 8 Common Security Mistakes that Make Your Business Vulnerable + Solutions
Mistake 1: Relying on Almost Ancient IT Infrastructure
Are you still running critical systems on a server that could be the great-grandfather of TikTok? Or worse – a peer of MySpace? Nothing personal, we are not trying to call you old – you just have a wealth of experience, though not necessarily in the protection and prevention of security mistakes. Let us remind you that outdated IT infrastructures are like the Klondike for cybercriminals – they attract them like a magnet with the promise of gold and riches. Even worse, it is like hackers have discovered a modern, fully furnished building… that is completely unlocked and has no security guard. Yes, it is time to replace your old, outdated hardware and unsupported software, because they are practically an open invitation to malicious actors and cyber disasters.
The Solution: No matter how nostalgic you are about your beloved computer running Windows 2012, it is time to let it enjoy a well-deserved retirement. Modern businesses need modern IT infrastructure. It might sound expensive and labor-intensive, but it really is not.
The best solution in this case is to choose IaaS (Infrastructure as a Service). This means you can support your business with a cloud-hosted infrastructure that guarantees security and can adapt to your business’s needs as it grows. One of the most popular and in-demand services we offer as part of our Managed IT Services Model is precisely related to the maintenance, security enhancement, and updates of IaaS systems.
Mistake 2: Weak Password Policies
Weak, long-used, and easy-to-guess passwords are undoubtedly the number one reason why hackers and cybercriminals gain easy access to your business systems in seconds. Let’s be honest – even for us, without being hackers, it is easy to guess your password if it is “CompanyName2022,” “password,” or “12345678.”
Don’t be careless when choosing and updating the passwords for your business systems if you don’t want to become part of the statistics of millions of megabytes of sensitive data leaked to the dark web after yet another cyberattack. In addition to choosing a password that is hard to guess or hack, it is essential to consider MFA (Multi-Factor Authentication).
The Solution: MFA is one of the easiest yet most effective cybersecurity methods you can implement for your business. This two-factor system means that even if a hacker manages to guess your password, they will be faced with a second layer of protection that is difficult or nearly impossible to breach because it requires a second action to verify identity.
Mistake 3: The Belief That Your Employees “Would Never Fall for That”
Every time you receive a letter from a Nigerian prince promising you untold riches and his entire inheritance, you probably think no one in their right mind would fall for such an obvious scam. But would they really not fall for it? Especially considering that online scams are becoming more and more cleverly crafted. Perhaps among your employees, there is someone curious enough to click on exactly the link they shouldn’t.
Today, phishing and scam emails look far too realistic and can easily deceive even the most observant and experienced individuals. In fact, it only takes one person. One click on the wrong link, one download of the wrong file, one wrong move. And your entire system is compromised.
The Solution: It’s not enough to rely solely on multi-factor authentication, firewalls, and antivirus systems. You also need to ensure that your employees fully understand how to protect themselves and your business from cyberattacks and avoid easily preventable security mistakes. This means you need to provide them with up-to-date training that helps them realize they are also a critical part of maintaining security.
Mistake 4: Lack of Continuous Monitoring and Maintenance
You have secured the safety of your business systems by hiring the right IT support specialists. But what happens when their working hours are over? Who monitors, observes, and maintains security? Hackers certainly don’t respect your working hours. In fact, they usually operate outside of them. Without constant monitoring and maintenance, not only are you more vulnerable to hacker attacks, but security mistakes and breaches can go unnoticed for days, which significantly complicates the situation.
The Solution: Choose a reliable service provider that can offer round-the-clock monitoring and maintenance of your systems. Our IT Monitoring and Maintenance services, part of our IT Operations Service, promise continuous observation and monitoring – no days off and not limited by working hours. This way, we can promptly inform you upon detecting suspicious activity, send alerts when potential threats are identified, analyze anomalies, and take countermeasures. Once we identify potential risks and problems, we don’t wait for something bad to happen, but proactively take care of the security of networks and systems. We provide updates to your systems and software with the latest and most reliable security fixes.
Mistake 5: Cloud Disasters and Chaos
The truth is that using cloud services is great and a top choice for many businesses. Cloud services are adaptable to the size and growth of a business, flexible, require significantly fewer expenses, and are convenient and efficient to use. However, it is mistakenly believed that they do not require maintenance and attention, and that they operate on autopilot, arranging and taking care of all the data and programs stored in them by themselves. Cloud services are not that kind of subscription service that you just set up and forget about. Such a service does not exist. To ensure that everything you use your cloud for is fully protected and optimized, you must also take care of the cloud itself.
The Solution: Cloud services are not just for data and software storage, but for their proper and well-protected management. Whether you or professionals will be responsible for your cloud’s security and management, you must ensure that cloud operation is never in conflict with current policies, settings, configurations, and best practices. Continuous cloud optimization is also required, including tracking unused resources, removing everything unnecessary and outdated. You must also control access to the cloud service and prevent access from individuals who may pose a potential security threat.
Mistake 6: You Have No Plan B in Case of an Incident
The harsh truth is this – cybersecurity mistakes and incidents are not a question of if they will happen, but when they will happen. Your job is to delay them for as long as possible and react appropriately when they inevitably occur. There are many reasons that can interfere with your systems or take them down completely. In such cases, good management is shown by knowing which specialists to contact, contacting them on time, having a Plan B for when the system is offline, clearly delegating responsibilities and tasks to your employees, and maintaining good and clear communication with all clients. To avoid chaos, an effective recovery plan is essential.
The Solution: Carefully and step by step plan your response to incidents with your system’s security and how to restore them as quickly as possible. You need to be aware of all steps well before the incident actually happens to avoid initial panic and confusion. That is why it is useful to cooperate with specialists in the field. They will identify critical systems and aspects, processes, and data, to make an accurate forecast of where problems might arise. They will develop an effective strategy to significantly reduce damage and ensure everything is restored as quickly as possible. They can also create and provide guidelines for the proper response to each type of incident, including clear instructions on the responsibilities of each employee and what each of them should do. In addition, specialists can test your systems’ security through simulated attacks to timely identify weak points and strengthen and correct them. Last but not least, they will create backups stored in a secure location that will greatly assist with fast and effective recovery in case of a real incident or problem.
Mistake 7: Underestimating Your Databases
Next on our list of common security mistakes is databases. Your databases are an extremely important and key part of your business. They store practically all critical information – from customer data, financial reports, to information on all internal business processes. Considering all this, do you want to neglect your database? Especially knowing that it is of particular interest to cybercriminals? In addition to being significantly more vulnerable to hacker attacks, neglected and poorly maintained databases are also significantly slower and less efficient, and often incompatible or non-compliant with current regulations.
The Solution: You must remember that preventing database problems is significantly easier, cheaper, and preferable to dealing with a problem once it arises. You need to rely on the right specialists for maintenance and effective management of your databases. This means selecting people with experience in optimizing and continuously monitoring databases so they can operate at high performance, be available whenever you need them, and be fully protected.
Mistake 8: Blind Belief That Just an Antivirus Program Is Completely Sufficient
We have bad news for you – if you rely on your antivirus system to save you from all possible attacks, then you are going into battle with lightsabers armed with a butter knife. Modern hackers are too well-equipped to be stopped with just an antivirus system.
The Solution: Protecting your systems in 2025 requires a multi-layered, proactive approach. Yes, you should not underestimate or forget about antivirus software, it is also necessary, but it is just a small part of your overall strategy. You need a full package of effective protection, designed and adapted to the needs of your business. This includes an approach for identifying suspicious behavior in real-time, capabilities for stopping threats before they happen. It is also necessary to implement a new generation of firewalls, a centralized system for analyzing security across your entire IT environment, identifying anomalies and promptly reporting potential threats and risks, constant vigilance, as well as systems for filtering phishing emails and suspicious links and files in the web space and emails.
The Recap on Security Mistakes
In conclusion, cybersecurity threats have evolved significantly. Your protection methods and systems must evolve alongside them. Want to learn more about our services and how we can ensure complete security for your business? Contact us today!




Leave A Comment